RAD Insights









Featured
.png)
August 18, 2025
RAD Security Joins NVIDIA Inception
RAD Security has joined NVIDIA Inception, a program that supports startups transforming industries with AI. Learn how RAD is using runtime context to make security smarter and more actionable.

August 18, 2025
RAD Security Joins NVIDIA Inception
RAD Security has joined NVIDIA Inception, a program that supports startups transforming industries with AI. Learn how RAD is using runtime context to make security smarter and more actionable.
.png)
August 1, 2025
#LaunchWeek Day 5: The GRCBot Is Ready for You
Day 5 of #LaunchWeek introduces GRCBot, a RADBot that pairs live runtime telemetry with policy and framework language to keep controls and evidence aligned in real time.

August 1, 2025
#LaunchWeek Day 5: The GRCBot Is Ready for You
Day 5 of #LaunchWeek introduces GRCBot, a RADBot that pairs live runtime telemetry with policy and framework language to keep controls and evidence aligned in real time.
.png)
July 31, 2025
#LaunchWeek Day 4: Cross-Stack Context from the RAD Signal Pipeline
Day 4 of #LaunchWeek adds Wiz, CrowdStrike, Okta, and Jira integrations, letting RADBots merge signals across tools for faster, context-rich security action.

July 31, 2025
#LaunchWeek Day 4: Cross-Stack Context from the RAD Signal Pipeline
Day 4 of #LaunchWeek adds Wiz, CrowdStrike, Okta, and Jira integrations, letting RADBots merge signals across tools for faster, context-rich security action.
.png)
July 30, 2025
#LaunchWeek Day 3: Ask RADBot Anywhere
Ask RADBot now answers security questions in Slack, the RAD Command Center, and every part of the RAD interface—returning runtime‑verified evidence in seconds.

July 30, 2025
#LaunchWeek Day 3: Ask RADBot Anywhere
Ask RADBot now answers security questions in Slack, the RAD Command Center, and every part of the RAD interface—returning runtime‑verified evidence in seconds.
All Insights
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

March 7, 2024
Container Deployment: Cloud Native Security Basics Part III
Learn the core concepts of container deployment, including Immutable Infrastructure, host security, patching, and container orchestration.

March 7, 2024
Jimmy Mesta
Container Deployment: Cloud Native Security Basics Part III
Learn the core concepts of container deployment, including Immutable Infrastructure, host security, patching, and container orchestration.
Cloud-Native Security
Cloud-Native Security Basics
Containers
Kubernetes

March 7, 2024
DevOps, Deployment & Container Orchestration | Cloud Native Security Part I
Learn more about cloud-native security, including DevOps culture and how to enable continuous integration and deployment into your DevOps strategy.

March 7, 2024
Jimmy Mesta
DevOps, Deployment & Container Orchestration | Cloud Native Security Part I
Learn more about cloud-native security, including DevOps culture and how to enable continuous integration and deployment into your DevOps strategy.
Cloud-Native Security
Cloud-Native Security Basics
Containers
DevOps
Kubernetes

March 6, 2024
Kubernetes RBAC: Role-Based Access Control
Dive into the basics of Kubernetes RBAC: role-based access control, including security principles like limiting Kubernetes cluster roles and permissions.

March 6, 2024
Jimmy Mesta
Kubernetes RBAC: Role-Based Access Control
Dive into the basics of Kubernetes RBAC: role-based access control, including security principles like limiting Kubernetes cluster roles and permissions.
Kubernetes
Role-Based Access Control
Zero Trust

March 4, 2024
FedRAMP Compliance Requirements for Enhancing SaaS Security
Achieve FedRAMP by providing assessment and insight into your cluster around your adherence to industry and government benchmarks, supply chain security and vulnerability management practices, use of RBAC and the Principle of Least Privilege.

March 4, 2024
Jimmy Mesta
FedRAMP Compliance Requirements for Enhancing SaaS Security
Achieve FedRAMP by providing assessment and insight into your cluster around your adherence to industry and government benchmarks, supply chain security and vulnerability management practices, use of RBAC and the Principle of Least Privilege.
Cloud-Native Security
Kubernetes

February 26, 2024
ITDR Best Practices Checklist for Cloud Native Security: Identity Threat Detection and Response
Learn about ITDR best practices and how cloud native identity identity threat detection and response can automate zero trust guidance for Kubernetes RBAC

February 26, 2024
Story Tweedie-Yates
ITDR Best Practices Checklist for Cloud Native Security: Identity Threat Detection and Response
Learn about ITDR best practices and how cloud native identity identity threat detection and response can automate zero trust guidance for Kubernetes RBAC
Detection and Response
Kubernetes
Role-Based Access Control
Zero Trust

February 2, 2024
What is Kubernetes Observability and Why it Matters in Cloud Native Security
Learn about Kubernetes and container security in this blog. With over 900,000 Kubernetes endpoints publicly exposed, it's important to mitigate risks.

February 2, 2024
Story Tweedie-Yates
What is Kubernetes Observability and Why it Matters in Cloud Native Security
Learn about Kubernetes and container security in this blog. With over 900,000 Kubernetes endpoints publicly exposed, it's important to mitigate risks.
Cloud-Native Security
Kubernetes

February 1, 2024
Container Escape: Addressing the New runC and BuildKit Vulnerabilities
Learn how to address the new runC and BuildKit vulnerabilities that affect your container runtime

February 1, 2024
Jimmy Mesta
Container Escape: Addressing the New runC and BuildKit Vulnerabilities
Learn how to address the new runC and BuildKit vulnerabilities that affect your container runtime
Cloud-Native Security
Containers
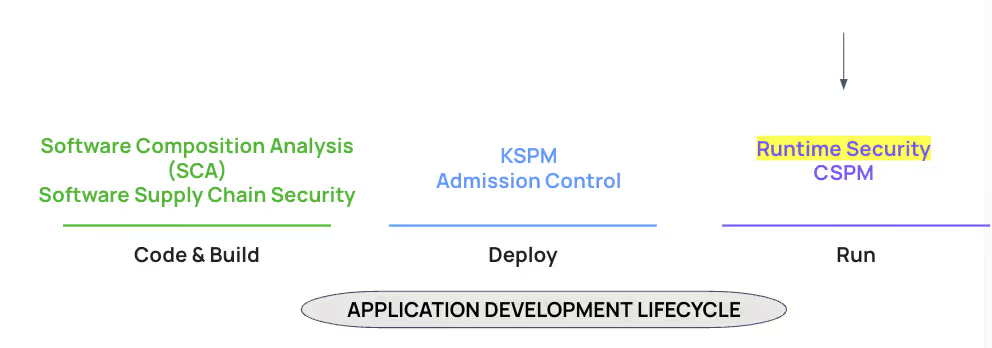
January 30, 2024
Best Practices for Container Runtime Security
Learn the best practices for runtime security and how to fortify your container environments against evolving threats with our essential guide.

January 30, 2024
Story Tweedie-Yates
Best Practices for Container Runtime Security
Learn the best practices for runtime security and how to fortify your container environments against evolving threats with our essential guide.
Containers
Zero Trust

January 9, 2024
2024 Cloud Native Security Predictions
2024 cloud native security predictions include increased scope for zero trust programs and more efficient software supply chain security

January 9, 2024
Brooke Motta
2024 Cloud Native Security Predictions
2024 cloud native security predictions include increased scope for zero trust programs and more efficient software supply chain security
Cloud-Native Security
News
No resources match your criteria.



