RAD Insights









Featured
.png)
August 18, 2025
RAD Security Joins NVIDIA Inception
RAD Security has joined NVIDIA Inception, a program that supports startups transforming industries with AI. Learn how RAD is using runtime context to make security smarter and more actionable.

August 18, 2025
RAD Security Joins NVIDIA Inception
RAD Security has joined NVIDIA Inception, a program that supports startups transforming industries with AI. Learn how RAD is using runtime context to make security smarter and more actionable.
.png)
August 1, 2025
#LaunchWeek Day 5: The GRCBot Is Ready for You
Day 5 of #LaunchWeek introduces GRCBot, a RADBot that pairs live runtime telemetry with policy and framework language to keep controls and evidence aligned in real time.

August 1, 2025
#LaunchWeek Day 5: The GRCBot Is Ready for You
Day 5 of #LaunchWeek introduces GRCBot, a RADBot that pairs live runtime telemetry with policy and framework language to keep controls and evidence aligned in real time.
.png)
July 31, 2025
#LaunchWeek Day 4: Cross-Stack Context from the RAD Signal Pipeline
Day 4 of #LaunchWeek adds Wiz, CrowdStrike, Okta, and Jira integrations, letting RADBots merge signals across tools for faster, context-rich security action.

July 31, 2025
#LaunchWeek Day 4: Cross-Stack Context from the RAD Signal Pipeline
Day 4 of #LaunchWeek adds Wiz, CrowdStrike, Okta, and Jira integrations, letting RADBots merge signals across tools for faster, context-rich security action.
.png)
July 30, 2025
#LaunchWeek Day 3: Ask RADBot Anywhere
Ask RADBot now answers security questions in Slack, the RAD Command Center, and every part of the RAD interface—returning runtime‑verified evidence in seconds.

July 30, 2025
#LaunchWeek Day 3: Ask RADBot Anywhere
Ask RADBot now answers security questions in Slack, the RAD Command Center, and every part of the RAD interface—returning runtime‑verified evidence in seconds.
All Insights
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

April 29, 2024
The 10 Female Cybersecurity Founders You Need to Follow
With RSA approaching, here are some female founders and leaders to follow who are leveling the playing field in cybersecurity.

April 29, 2024
Brooke Motta
The 10 Female Cybersecurity Founders You Need to Follow
With RSA approaching, here are some female founders and leaders to follow who are leveling the playing field in cybersecurity.
No items found.

April 17, 2024
Kubernetes Version 1.30 Security Features
This Kubernetes version 1.30 includes many security related features that will help with admission control, authentication, authorization and more.

April 17, 2024
Story Tweedie-Yates
Kubernetes Version 1.30 Security Features
This Kubernetes version 1.30 includes many security related features that will help with admission control, authentication, authorization and more.
Kubernetes
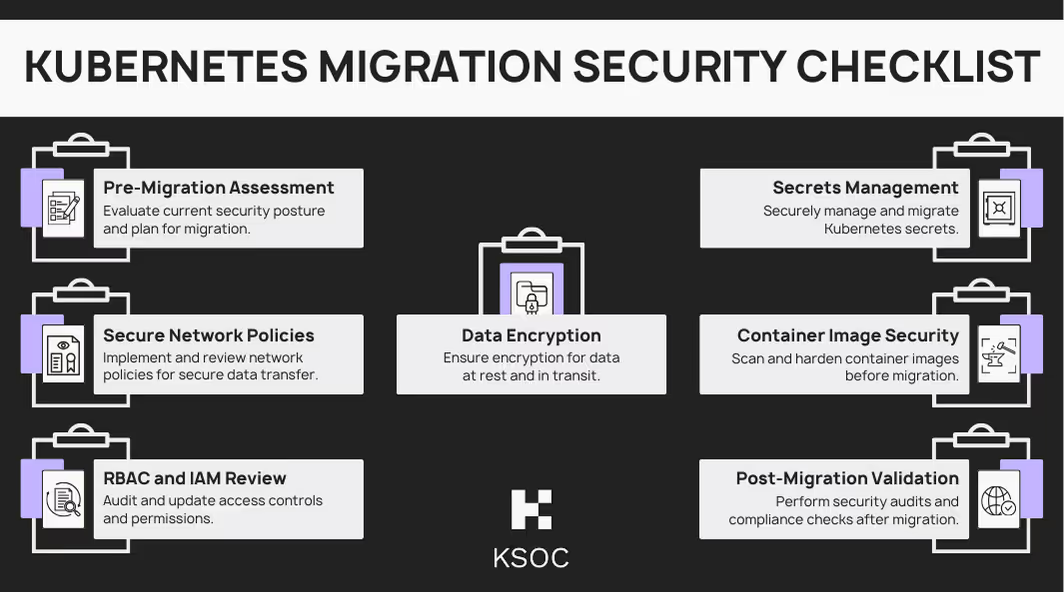
April 15, 2024
Kubernetes Migration Guide
Migrating to Kubernetes is a large undertaking and requires a security-first mindset to ensure that applications remain secure.

April 15, 2024
RAD Security
Kubernetes Migration Guide
Migrating to Kubernetes is a large undertaking and requires a security-first mindset to ensure that applications remain secure.
Kubernetes
April 4, 2024
RAD Security Integrates with Chainguard to Strengthen CVE Vulnerability Management Systems
As part of RAD Security's real-time Kubernetes posture management solution, you can now automatically track, and even enforce, the usage of Chainguard’s low-to-zero known CVE container images.

April 4, 2024
Jimmy Mesta
RAD Security Integrates with Chainguard to Strengthen CVE Vulnerability Management Systems
As part of RAD Security's real-time Kubernetes posture management solution, you can now automatically track, and even enforce, the usage of Chainguard’s low-to-zero known CVE container images.
Containers

March 30, 2024
XZ Backdoor (CVE-2024-3094) - What You Need to Know
CVE-2024-3094, otherwise known as the XZ Backdoor software supply chain attack, is considered the most sophisticated social engineering attack on open-source projects to date.

March 30, 2024
Jimmy Mesta
XZ Backdoor (CVE-2024-3094) - What You Need to Know
CVE-2024-3094, otherwise known as the XZ Backdoor software supply chain attack, is considered the most sophisticated social engineering attack on open-source projects to date.
Cloud Attacks
Security
March 12, 2024
Reimagining Cloud Native Detection & Response: KSOC's Evolutionary Shift to RAD Security
KSOC has evolved to RAD Security, signifying a new era of behavioral cloud native detection and response that can combat today’s evolving threats.

March 12, 2024
Brooke Motta
Reimagining Cloud Native Detection & Response: KSOC's Evolutionary Shift to RAD Security
KSOC has evolved to RAD Security, signifying a new era of behavioral cloud native detection and response that can combat today’s evolving threats.
Cloud-Native Security
Detection and Response
News

March 12, 2024
Securing Your Future in 2024: Grabbing a Piece of the K8s Security Pie
Kubernetes security is like an open invitation to further your career and make yourself an invaluable part of your company’s journey forward.

March 12, 2024
Brooke Motta
Securing Your Future in 2024: Grabbing a Piece of the K8s Security Pie
Kubernetes security is like an open invitation to further your career and make yourself an invaluable part of your company’s journey forward.
Kubernetes

March 8, 2024
KSPM: Kubernetes Security Posture Management Guide
This guide is a one-stop resource for KSPM, hardening your Kubernetes clusters, enhancing incident response capabilities, and implementing defense-in-depth measures.

March 8, 2024
Jimmy Mesta
KSPM: Kubernetes Security Posture Management Guide
This guide is a one-stop resource for KSPM, hardening your Kubernetes clusters, enhancing incident response capabilities, and implementing defense-in-depth measures.
KSPM
Kubernetes

March 7, 2024
Kubernetes Administration: Cloud Native Security Basics Part V
Understand how to effectively interact with Kubernetes as an administrator in this basic guide to securing your environment.

March 7, 2024
Jimmy Mesta
Kubernetes Administration: Cloud Native Security Basics Part V
Understand how to effectively interact with Kubernetes as an administrator in this basic guide to securing your environment.
Cloud-Native Security
Cloud-Native Security Basics
Kubernetes

March 7, 2024
Introduction to Kubernetes: Cloud Native Security Basics Part IV
Uncover the main components of Kubernetes, including clusters, control planes, API servers, Nodes, and Pods.

March 7, 2024
Jimmy Mesta
Introduction to Kubernetes: Cloud Native Security Basics Part IV
Uncover the main components of Kubernetes, including clusters, control planes, API servers, Nodes, and Pods.
Cloud-Native Security Basics
DevOps
Kubernetes

March 7, 2024
Kubernetes Security Checklist: Cloud Native Security Basics Part VI
This Kubernetes security checklist provides cloud-native security best practices for Kubernetes admission control, audit logging, and more.

March 7, 2024
Jimmy Mesta
Kubernetes Security Checklist: Cloud Native Security Basics Part VI
This Kubernetes security checklist provides cloud-native security best practices for Kubernetes admission control, audit logging, and more.
Cloud-Native Security Basics
Kubernetes

March 7, 2024
Container Security: Cloud Native Security Basics Part II
Container security requires understanding the significant advantages of containers over traditional virtual machines, as well as container architecture

March 7, 2024
Jimmy Mesta
Container Security: Cloud Native Security Basics Part II
Container security requires understanding the significant advantages of containers over traditional virtual machines, as well as container architecture
Cloud-Native Security Basics
Containers
Kubernetes
No resources match your criteria.



